Attacks by state-sponsored threat actors are increasing: fact.
Incidents like 2017’s WannaCry attacks by suspected North Korean threat actors and the more recent news about Russian hackers taking control of hundreds of thousands of network routers worldwide spooked the enterprise community.
The Australian Government pro-actively legislated effective July 2018 that critical infrastructure asset owners are now within reach of government experts to proscribe network security investments. Japan has a comparable cyber security posture as it builds new cyber assets for the coming Summer Olympics in 2020.
Based on evidence, the state sponsored attacks go beyond espionage and cause service disruptions and actual physical harm to the victim organisations. Recent real examples of malware campaigns are TRITON / TRISIS and Industroyer / CrashOverride – designed to disrupt critical industrial processes – attacks on the electricity grid are fuelling fears.
The Sofacy group remains a persistent global threat. Unit 42 continues to target multiple organisations throughout the world with a strong emphasis on government and civil institutions.
In May 2018, the FBI disclosed that Russian persistent threat actor, the Sofacy group, had managed to infect more than 500,000 home-office routers and network attached storage devices worldwide with malware for remotely controlling them.
Many security experts have expressed concern that infected devices could be used to launch DDoS and other attacks against organisations worldwide.
Data exfiltration is another area of concern.
Bad actors use data exfiltration techniques to transmit stolen information back to head office. Often the DNS is used as a protocol to accomplish exfiltration. Exploiting DNS tunnels allow users to access the internet utilising the unmetered DNS protocol without paying for the data they use.
TunnelGuard by Secure64 detects and blocks attempts to exfiltrate data; originally designed for a different use case – bandwidth theft – it is equally adept at stopping exfiltration via the DNS.
Now in some countries, carriage service providers are required to prevent the exfiltration of data.
Secure64 DNS TunnelGuard is part of a family of DNS-based security services that protect the network and its users. DNS TunnelGuard is an on-box security service that uses sophisticated and proprietary technology to detect and automatically block the most common DNS tunnels, including Iodine, dns2tcp, dnscat2, OxymanDNS and others, with a high degree of accuracy, and minimal impact on DNS performance.
December 2017, we read that a threat actor used a sophisticated malware tool dubbed Triton / Trisis to disrupt operations at a critical infrastructure facility in the Middle East.
Cyberattacks that cause physical damage to critical infrastructure — like the Stuxnet campaign that destroyed nearly 1,000 centrifuges at an Iranian uranium enrichment facility in 2010 — have been relatively rare because of how difficult they were to carry out. That probability may be changing quickly for the worse.
In boardrooms, Energy and oil and gas companies have expressed concern from cyberattacks causing catastrophic physical harm, such as explosions, at their facilities.
Concerns over nation-state attacks are certainly not limited to Europe and South Asia. A similarly high degree of apprehension over the threat exists among US companies and organisations elsewhere.
Nation-state cyberattacks are not a geographically limited problem.
It is no surprise, critical infrastructure organisations are more concerned about the threat because of the negative impact of a successful attack on operations and reputation from citizens and shareholders.
Despite organisations’ confidence to mitigate state sponsored attacks — malware or DDOS attacks — the simple fact is that successful attacks continue to take place. Consistently and comprehensively implementing foundational security controls is the best way to reduce your risk.
Depending on your sensibilities, defacement of ccTLD websites are an annoyance or an indicator of cyber security vulnerability.
How do hackers deface a website? Using SQL injection allows an unauthorised user to gain administrative access.
The impact of SQL injection attacks varies from gathering of sensitive data to manipulating database information, and from executing system-level commands to denial of service of the application.
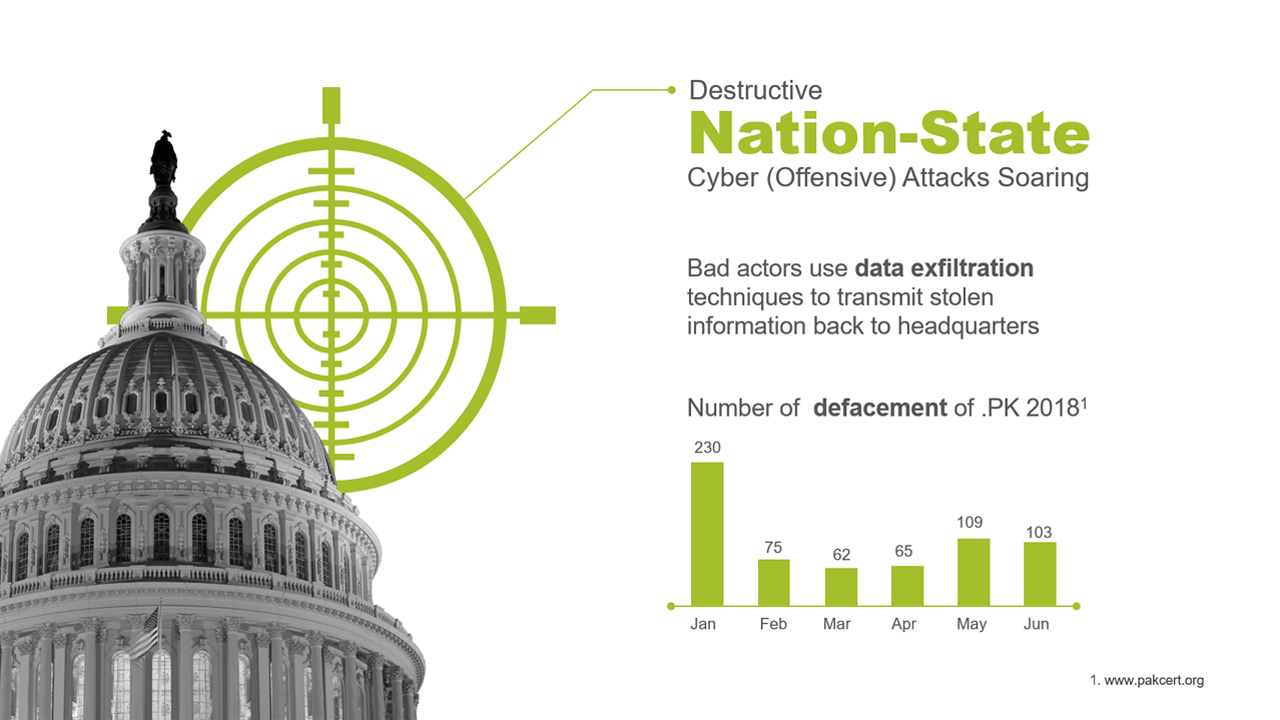
Simply, defacement of government institution websites is evidence of ongoing malicious, advanced persistent threat attacks by Nation-State actors and hacktivists.
Compromised IoT Devices Will Be a Source of Attacks
Without sounding too alarmist, the emergence of Internet of Things devices has created exponential growth in attacks.
The evidence informs us that the IoT will be a major source of cyber security risk.
Based on Symantec’s analysis, we saw a 600% increase in attacks in 2017 over 2016.
The source of IoT attacks will come from several country domains but we can also plan that internal attacks will become more significant in the near-term.
Secure64 from C-COR is the first line of defence from Nation-State Cyber Attacks.
